As a new report shows, cyber criminals continue to rely on business email compromise in addition to ransomware and use long-known, unpatched vulnerabilities for attacks. The report shows that ransom demands are becoming increasingly outrageous.
The Arctic Wolf Labs Threat Report was created based on threat, malware, digital forensics and incident response case data that Arctic Wolf collects across the security operations framework. It provides deep insights into the global cybercrime ecosystem, highlights global threat trends, and provides strategic cybersecurity recommendations for the coming year.
Ransomware claims increase by 20%
Cybercrime has developed into a real business in recent years, with offerings such as ransomware-as-a-service leading to a real “democratization” of the criminal business. Even threat actors without technical know-how can carry out attacks. At the same time, ransomware groups are becoming increasingly aggressive. Manufacturing, services, and education/non-profit sectors were the three industries that appeared most frequently on ransomware leak sites.
In light of international law enforcement efforts and increasing non-payment by victims, the groups are also expanding their list of targets and looking for ways to put even more pressure on victims. The average initial ransom demand rose by 20% to $600.000 compared to the previous year. The public sector, retail, energy and legal sectors each recorded average claims of $1 million or more.
Ransomware groups are coming under increasing pressure
The dismantling of the Lockbit hacker group in “Operation Cronos”, in which international investigators worked together, including the NCA, FBI and Europol, is a current example of ransomware groups coming under increasing pressure. But unfortunately this destruction will most likely only have a short-term effect. Of the large ransomware group, which extorted an average of 1,3 victims per day, only six people were identified and only two of them were arrested. It can therefore be assumed that the same actors will quickly operate again under different names. Great vigilance is therefore still required.
Business Email Compromise remains popular – and less studied

🔎 Top 10 vulnerabilities: More than half of the incidents Arctic Wolf investigated exploited at least one of the following 10 vulnerabilities (Image: Arctic Wolf).
Ransomware may make more headlines, but BEC incidents are effective and much easier to execute. Additionally, typically only the most serious BEC incidents – such as those involving account compromise or other access attempts – result in a full Incident Response (IR) investigation. A ransomware incident is 15 times more likely to lead to an investigation than a BEC incident, even though BEC incidents outnumber ransomware incidents by a factor of 10.
Nonetheless, as in the previous year, BEC incidents accounted for nearly 30% of all incidents investigated by Arctic Wolf® Incident Response during this reporting period, underscoring how much they continue to pose an everyday threat to organizations.
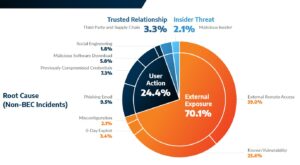
Known vulnerabilities cause 60% of security incidents
In 29% of the non-BEC incidents Arctic Wolf investigated, the attackers exploited a vulnerability in an externally accessible system. In nearly 60% of these incidents, this was a vulnerability that was identified as early as 2022 or earlier, meaning organizations would theoretically have had months to years to patch the affected system or remove (or further secure) external access. Only 11,7% of these non-BEC incidents – or 3,4% of incidents overall – contained a zero-day vulnerability, a previously unknown security risk.
About Arctic Wolf
Arctic Wolf is a global leader in security operations, providing the first cloud-native security operations platform to mitigate cyber risk. Based on threat telemetry spanning endpoint, network and cloud sources, the Arctic Wolf® Security Operations Cloud analyzes more than 1,6 trillion security events per week worldwide. It provides company-critical insights into almost all security use cases and optimizes customers’ heterogeneous security solutions. The Arctic Wolf platform is used by more than 2.000 customers worldwide. It provides automated threat detection and response, enabling organizations of all sizes to set up world-class security operations at the push of a button.
Matching articles on the topic
This post was originally published on 3rd party site mentioned in the title of this site